Архивы за 16.03.2016

Сброс и настройка Cisco ASA 5505/5520
0
Handles instruction
1st reset by pressing ESCAPE at the same time with boot proccess and login in ROM Monitore mode. You will see rommoon prompt (rommon#0>).
The enter command «confreg»- it's register settings.
rommon #0> confreg
rommon #1>confreg 0×41 (then after configuration need to set confreg 0×1 — its normal booting )
Reset the appliance with the boot command:
rommon #2>boot
When finishing booting proccess you will see User Mode prompt (>):
ciscoasa>
Then enter in Privileged Mode prompt: (#)
ciscoasa>ena (enable)
Password:
ciscoasa#
Then copy startup config to running configuration:
ciscoasa#copy startup-config running-config
Destination filename [running-config]? Press yes [y]
or just «wr».
----
To configure VLAN 1 for LAN. (or INSIDE)
interface Vlan1
description Local LAN
nameif LAN
security-level 100
ip address [private ip add and mask]
no shutdown
To configure VLAN 2 for WAN (or OUTSIDE).
interface Vlan2
description WAN
nameif WAN
security-level 0
ip address [external IP add and mask]
no shutdown
Security leval means:
Security level 100
The highest possible level and most trusted, it is used by the inside interface by default.
Security level 0
The lowest possible level, most untrusted, it’s used by the outside interface by default.
----
Configure then defaulr route:
route WAN 0.0.0.0 0.0.0.0 [GW for the network]
------------
Configure DNS:
dns domain-lookup WAN (enable dns function)
dns nameserver 8.8.8.8 8.8.4.4 (or other DNS, can be your local)
---
Configure SSH:
ssh 0.0.0.0 0.0.0.0 WAN (all ssh access via WAN interface)
ssh version 2
crypto key generation rsa modules 2048 (use longest for more security)
aaa authentication ssh console LOCAL
-----
Create logins:
username [the name of user] password [password of the user] — access for Privileged Mode
enable password [password] — acess for User Mode
--------
Don't forget to save your settings — «wr»
Then check ping and SSH.
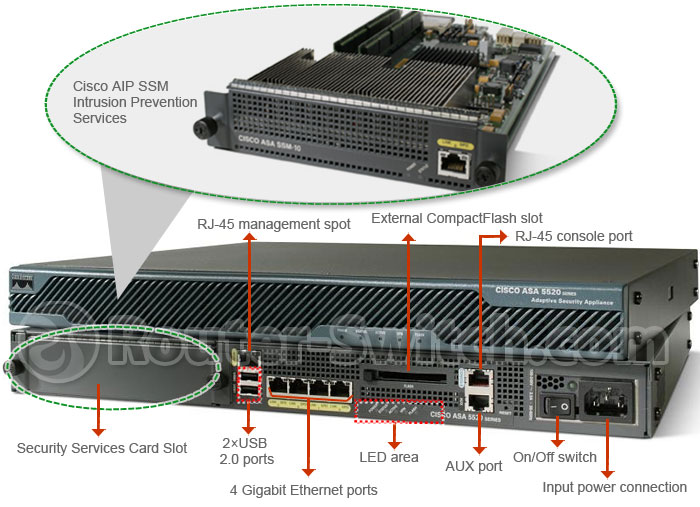
Cisco ASA 5520
interface GigabitEthernet0/0
description WAN
nameif OUTSIDE
security-level 0
ip address *.*.*.*
!
interface GigabitEthernet0/1
description LAN
nameif INSIDE
security-level 100
no ip address
!
interface GigabitEthernet0/2
description LAN
nameif INSIDE2
security-level 100
no ip address
!
interface GigabitEthernet0/3
description LAN
nameif INSIDE3
security-level 100
no ip address
!
interface Management0/0
shutdown
no nameif
no security-level
no ip address
dns domain-lookup OUTSIDE
dns server-group DefaultDNS
name-server 8.8.8.8
name-server 8.8.4.4
access-list inside_access_out extended permit ip any any
logging enable
logging host OUTSIDE *.*.*.*
mtu OUTSIDE 1500
mtu INSIDE 1500
mtu INSIDE2 1500
mtu INSIDE3 1500
route OUTSIDE 0.0.0.0 0.0.0.0 *.*.*.* 1
user-identity default-domain LOCAL
aaa authentication ssh console LOCAL
aaa authentication telnet console LOCAL
snmp-server host OUTSIDE *.*.*.* community ***** version 2c
snmp-server location Moscow
telnet 0.0.0.0 0.0.0.0 INSIDE
telnet timeout 5
ssh 0.0.0.0 0.0.0.0 OUTSIDE
ssh timeout 5
ssh version 2